Monitor and secure AD with comprehensive Active Directory auditing tools. Active Directory continues to be the cornerstone for securing access to business-critical applications. Yet change reporting and vulnerability monitoring for AD is cumbersome, time-consuming, and often impossible using system-provided IT auditing tools. Adopting Azure AD only increases your reliance on Active Directory, while doubling the attack surface and introducing additional opportunities for ransomware and other exploits. This often results in data breaches and insider threats that can go undetected without protections in place. Fortunately, Change Auditor provides real-time threat monitoring and security tracking of all key user activity and administrator changes.


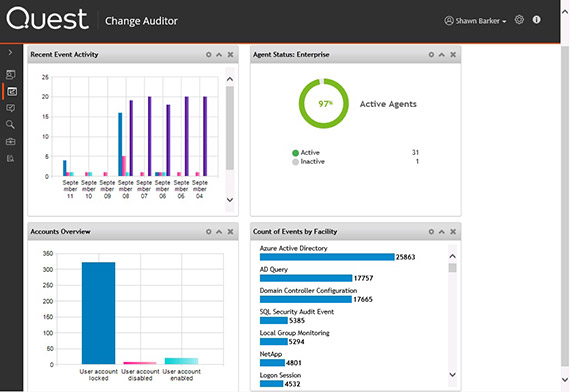
Change Auditor is a complete set of real-time Active Directory auditing tools offering in-depth forensics and security threat monitoring on all key configuration, user and administrator changes in your AD environment. Change Auditor tracks Active Directory changes and detects indicators of compromise (IOCs) across AD and Azure AD to thwart attackers and their attempts to deploy ransomware. Additionally, Change Auditor tracks lateral movement of adversaries across the network and audits suspicious user activity.
Audit all security changes across your AD and Azure AD environments, including user and group changes, as well as exploits such as DCSync and DCShadow attacks, AD database exfiltration, and SIDHistory use.
Detect threats early – including unauthorized domain replication, offline extraction of your AD database, and domain-level GPO linking – to mitigate and avoid costly ransomware attacks.
Block attackers from making changes to critical groups, GPO settings and linking or exfiltrating your AD database to steal credentials – regardless of the privileges they’ve hijacked.
Track Active Directory changes with a detailed audit trail of every change made to AD and Azure AD, including who made them, without the blind spots of built-in auditing functions.
Experience comprehensive Active Directory auditing tools offering everything from upfront vulnerability assessment to intrusion detection and monitoring of compromised accounts. Change Auditor has you covered at every step.
Translate cryptic system-provided logs into a simple, normalized format highlighting the who, what, when, where and workstation details, and before and after values.
Send critical change and pattern alerts to email and mobile devices to prompt immediate action, even while you're not on site.
Capture the originating IP address/workstation name for account lockout events to simplify troubleshooting.
07:25
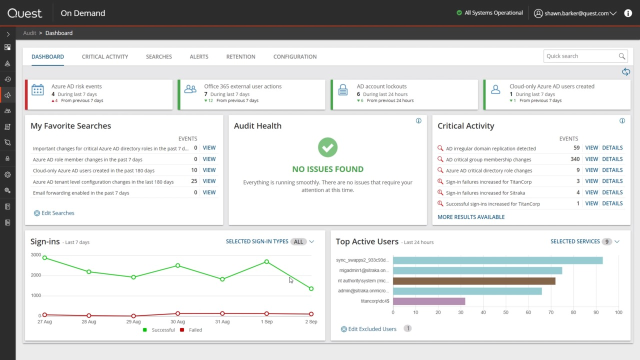
Pair Change Auditor with On Demand Audit to get a single, hosted security dashboard of all vulnerabilities and suspicious activity across AD, Azure AD, Exchange Online, SharePoint Online, OneDrive for Business and Teams. On Demand Audit proactively highlights security threats and anomalous activity and accelerates incident investigations through contextual and interactive data visualizations.
Detect attack attempts, lateral movement through your network, and post-attack damage done to your critical workloads like Exchange and file systems with this comprehensive set of Active Directory auditing tools.
View, highlight and filter change events and discover their relation to other threat events in chronological order across your AD and Azure AD environment for better forensic analysis and security incident response.
Use this comprehensive set of Active Directory auditing tools for instant, one-click access to all information on the change you're viewing and all related events, such as what other changes came from specific users and workstations, eliminating guesswork.
Track Active Directory changes without the need for system-provided audit logs, eliminating blind spots, and resulting in increased visibility of suspicious user activity.
Restore previous values on unauthorized, mistaken or improper changes with the click of a button, directly from the Change Auditor console.
Identify Tier Zero assets and the attack paths to them using BloodHound Enterprise and monitor and secure those attack paths to avoid exploits with Change Auditor.
Enrich SIEM solutions including Sentinel, Splunk, ArcSight, QRadar or any platform supporting Syslog by integrating Change Auditor’s detailed activity logs.
Generate comprehensive reports to support regulatory compliance mandates for GDPR, PCI DSS, HIPAA, SOX, FISMA / NIST, GLBA and more.
Change Auditor object protection is a lifesaver. I have it set up to prevent changes to the ACLs on certain directories on our file servers, as well as to protect all administrative accounts. We’ve had pen testers come in and be very surprised that they could not get past the Change Auditor object protection
Enterprise Administrator, Large Retail Chain Read Case Study
With Change Auditor, we achieved our goal of gaining complete and centralized visibility of security audit operations across the entire Group — including not just our on-premises Windows file servers and domain controllers but also our Office 365 services, such as mail, SharePoint Online and OneDrive for Business
Mirco Destro CIO and IT Manager, AFV Beltrame Group Read Case Study
Previously, investigating an issue could easily take an hour. Change Auditor cuts that time to just 5–10 minutes.
Dennis Persson IT Systems Technician, Region Halland Read Case Study